Allow Administrators to login to NoTouch Center using LDAP in Active Directory and Azure AD
Contents
- 1 General information
- 2 Parameters
- 3 Rolefilter Idea/Infos
- 4 Tool for testing your LDAP string
- 5 Azure AD \ LDAP support
- 6 Special eDirectory settings
- 7 Windows AD \ LDAPS
- 8 Troubleshooting
General information
NoTouch Center is a tool for system administrators to manage their endpoints. It not only maintains a list of local user accounts, but it also supports user authentication via the Lightweight Directory Access Protocol (LDAP) using either Microsoft's Active Directory or Novell's eDirectory. So, if you want to allow several sysadmins to access NoTouch Center without having to create accounts for them in NoTouch Center, this is what you need.
- As of NoTouch Center 4.5.+ you can also add MFA (Multifactor Authentication)
Note: This feature is intended for enterprise usage. If you have just a few persons working with NoTouch Center, you are probably better off using local accounts as LDAP creates another dependency, to the LDAP server.
Even when using LDAP authentication, local accounts such as the "admin" user will still work so you can still log in to NoTouch Center in case the LDAP server fails. However it means that you should choose a good password for local accounts, especially the admin user. Do not use something like "admin", "test", "notouch" or so that is easy to guess.
Parameters
** When making changes to LDAP configuration, it is important that you restart the NoTouch Center Service. Any changes to the LDAP configuration will NOT apply without restarting the service. The Service can easily be restarted from the Virtual Appliance Administration page**
You will find the LDAP configuration parameters in NoTouch Center under "Configuration" (the yellow icon top-right corner) and "Authentication": NoTouch Center Settings
 This is the Global Settings Icon. Once you clic on this, in the window presented, you will see the "Module" selection that you can set to "LDAP".
This is the Global Settings Icon. Once you clic on this, in the window presented, you will see the "Module" selection that you can set to "LDAP".
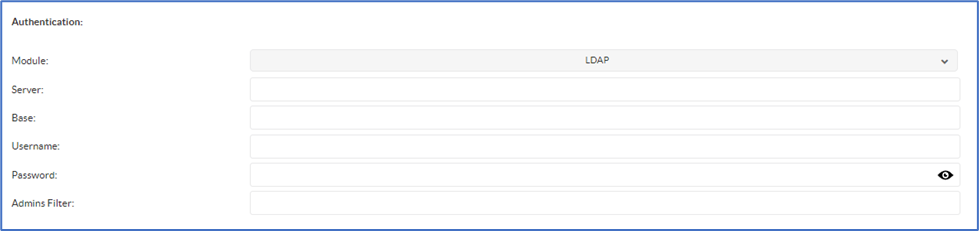
| Server: | Enter your LDAP server (note: for secure LDAP, add the prefix ldaps://) |
| Base: | Base: Specify the Base Organizational Unit (OU) for user searches (e.g., OU-parentOU,dc=myCompany,dc=com). This must direct to an OU or Parent OU that contains user accounts; pointing only to the domain's base Distinguished Name (DN) will not work. |
| Username: | Your valid username for the LDAP server (if no username is defined, your NoTouch Center logon is used instead). This refers to an account that has the privileges to query the LDAP server. Please use UPN format (username@domain). |
| Password: | Your valid password for the user specified above (if no password is defined, your NoTouch Center logon password is used instead) |
| Adminfilter: | LDAP filter for NoTouch Center admin users.
All AD accounts that this filter contains will be logged in as 'admins'. e.g.: (&(memberOf=CN=ADMINGROUP,OU=user,DC=myCompany,DC=com)(userPrincipalname=%user%)) Depending on LDAP configuration you may need to use a filter similar to this, Note without the (Brackets) CN=ADMINGROUP,OU=user,DC=myCompany,DC=com |
| Helpdeskfilter: | LDAP filter for NoTouch Center helpdesk user.
All AD accounts that this filter contains will be logged in as 'helpdesk'. e.g. (&(memberOf=CN=HELPDESKGROUP,OU=test,OU=user,DC=myCompany,DC=com)(userPrincipalname=%user%)) |
| Rolefilter: |
All AD accounts that this filter contains will be logged in with the corresponding rights of the defined role. LDAP filter for a NoTouch Center user role. A user role is part of the Permissions management feature |
Note: If you use 'userPrincipalname' in your filter, the users must use the full domain username to log on (for example 'testuser@mycompany.com'). If you want to use the username only (in this case: 'testuser'), please use 'sAMAccountName' instead!
Multiple Ldap security groups
if you would like to setup multiple security groups with different access levels. First create a security group in AD for each group of uses. next Create an Identically named Role in NTC for each security group and assign permissions for each. Lastly for each Role you created in NTC expand the Authentication Configuration section and enter the CN,OU,DC of the AD security Group
ex. Helpdesk Role
(&(memberOf=CN=HelpDesk,OU=SECGroupOU,DC=YourDomain,DC=com)(sAMAccountName=%user%))
ex. FullAdmin Role( you will still need a role configured for full admin but the filter should be blank on the role and instead the role should be set under the global ldap settings in NTC)
(&(memberOf=CN=FullAdmin,OU=SECGroupOU,DC=YourDomain,DC=com)(sAMAccountName=%user%))
Note1: after the above is complete under your main LDAP setting in NTC clear out the Admins Filter field and save changes and then reboot NTC
Note2: If you use 'userPrincipalname' in your filter, the users must use the full domain username to log on (for example 'testuser@mycompany.com').
If you want to use the username only (in this case: 'testuser'), please use 'sAMAccountName' instead!
Role filter Idea/Infos
You add a group (e.g. OmahaAdmin) in your active directory and assign users to that group. Create an identical role in your NoTouch Center and define your rights for this role as next step. Each user of your active directory group (e.g. OmahaAdmin) can now logon with the right's assigned to your identical NoTouch Center role Note: After saving / changing your LDAP configuration with the "save" button, you have to restart your NoTouch Center!
Tool for testing your LDAP string
Tools for your LDAP filters may be found here Also, Here are some additional tools that may assist
Azure AD \ LDAP support
To integrate NoTouch Center with Azure AD you will need to utilize Azure AD Domain Services
Special eDirectory settings
If you are using Novell eDirectory, the root certificate of the directory server has to be imported into the local certstore on the NoTouch Center server like this:
keytool -import -trustcacerts -alias t1 -file ca.crt -keystore /etc/truststore -storepass liscon
The rest of the configuration is the same as the ActiveDirectory configuration above.
Windows Active Directory Ldaps (Secure Ldap)
The server field in the NTC ldap settings MUST be the FQDN and not the IP address of the domain controller. make sure that you can ping the FQDN from the NTC server and that it's pinging the correct IP Address
- You can use any third party certificate you like . the certificate must have the FQDN of the domain controller as either the Common Name or Subject Alternative Name. the certificate must also be installed in the Computer Certificates / Personal Store
- The certificate MUST also be stored in the Keystore of the NTC Server using the following command.
keytool -import -trustcacerts -alias t1 -file ca.crt -keystore /etc/truststore -storepass liscon
if you are replacing a certificate you can remove the existing certificate first with
sudo keytool -delete -alias t1 -keystore /etc/keystore -storepass liscon - You need to restart the NTC service after ANY change to the Ldap Settings for them to become active!
Troubleshooting
If you would like to test your query strings please use the above-mentioned LDAP tool. If your queries work in the query tool but not in NoTouch Center, try giving the NoTouch Center LDAP user local administrator rights on the NoTouch Center machine.
- Ensure you can ping the FQDN (ldaps) / IP (ldap) of the domain controller from you NTC Server
- Make sure if using LDAPS that you are using valid certificates containing the FQDN of the domain controller in the Common Name or Subject Alternative Names ex. dc1.yourdomain.com
- Make sure the Ldap Filters have been used properly in the NTC Roles and that proper permissions have been assigned.
