The Virtual Appliance comes with a firewall that is configured appropriately by default and can be modified to filter additional services
The Stratodesk Virtual Appliance comes with a host firewall similar to any other contemporary server system. It is based on Linux' iptables mechanism and will filter inbound packets and allow only packets to selected services go through.
Contents
Firewall configuration
Log in to the appliance web console, and go to "VA Operation" -> "Firewall" to see this screen:
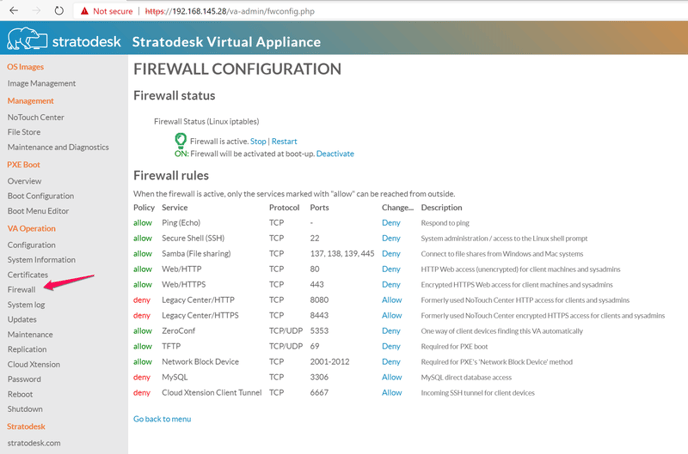
The actual configuration is straightforward and consists of fixed allow/deny rules. Turning the firewall off means to allow ALL access.
The default configuration for new setups is to allow all selected services except the two "Legacy Center" services. If you experience problems with older client versions that may not Announce as expected, consider opening these ports up until things work, then set the URL Prefix correctly and finally turn the services off.
The two Legacy Center services refer to the original NoTouch Center ports 8080 and 8443. With the Reverse proxy it is not necessary to expose them to the outside world. For older installations, it may be necessary though, either because the URL Prefix contains an 8080 or 8443 number or clients are too old to automatically try 80/443.
Firewall notes
The firewall "allow" rules include a rule for "related and established" traffic. That means, if you switch for example from Allow to Deny, open connections will not be interrupted. This will manifest in two things, for instance.
- If you have a continuous ping running, it will not stop. However, if you interrupt it after changing to "deny", and start a new ping, the new ping will not go through.
- If you disable the WWW port you are currently connecting to, your browser session will continue for a while. However, if you close the browser tab after changing to "deny", and then go to the same URL again, it will not work anymore.
Hint: Do not set everything to "deny" at once. If you play with the firewall settings, leave at least SSH open for recovery (see below). You will lock yourself out permanently if you disable ALL these services. If you do so, you will have to scrap the Virtual Appliance or undergo a complicated unsupported boot-loader-modification-procedure inside your hypervisor console. Don't do it.
Textual access
If you lock yourself out, e.g. by disabling both the HTTP and HTTPS ports, you can log in via SSH, become root, and modify the files in /etc/stratofw. The subfolder avail contains stanzas for all available rules, the subfolder enabled contains links to the stanzas in avail, only if the stanza is supposed to be included. Linux people will be reminded of how Apache and other services are configured in Debian/Ubuntu-based systems. We provide command shortcuts to create or delete the symlinks:
/opt/bin/fwsvcon SERVICE
enables a services, while
/opt/bin/fwsvcoff SERVICE
disables a specific service. These services are available: 010_icmpecho, 100_ssh, 200_samba, 300_http, 310_https, 350_legacyhttp, 360_legacyhttps, 390_zeroconf, 400_tftp, 410_nbd. The numbers are sequence numbers, and the names are self-explanatory.
To regenerate the firewall configuration from these links, call
/opt/bin/generatefwconfig
Also, you can call /opt/bin/fw-start and /opt/bin/fw-stop to start and stop the Firewall (remember: Firewall stopped = full access).
Note: The "actual firewall configuration" of course goes into /etc/iptables/rules.v4. However, it makes no sense to edit /etc/iptables/rules.v4 directly, because your changes will be overwritten. Use the mechanism above instead.
Help! I locked myself out
- Log in to the system via SSH as user notouchadm with your admin password (as described in more detail here: SSH#Logging in 2
- Get root permissions by issuing this command (as described in SSH#Gaining root privileges):
- sudo su
- and entering your password again
- Type in and hit enter afterwards:
- /opt/bin/fwsvcon 300_http
- Type in and hit enter afterwards:
- /opt/bin/generatefwconfig
- Reboot the VA or type in:
- /opt/bin/fw-stop ; /opt/bin/fw-start
I want to add custom rules
We assume you know the Linux iptables mechanism and can understand our ruleset and how our generation mechanism works:
- Simply place a file with a sequence number in /etc/stratofw/avail
- Make sure the file contains a proper iptables command portion that can go into the rules.v4 file
- Create a symlink in /etc/stratofw/enabled with the same filename to your file in /etc/stratofw/avail
- Regenerate the firewall configuration and restart the firewall (see above)
