NoTouch supports provisioning and advanced configuration of Network Authentication and the required certificates
There are so many different ways how network authentication for wired and wireless networks can be handled. Almost all of them are handled by software package named wpa_supplicant - a standard Linux program that is present in major distributions and also in the Stratodesk platform. Configuring wpa_supplicant means configuring network authentication, WPA2 with or without certificates, IEEE 802.1X.
(Please note that this article is specifically meant for WPASupplicant. There is are also network authentication options in the "Ethernet" and "WLAN" subsections of each interface - those are "lightweight" and should be much easier to configure. By going to "WPASupplicant" and saying "Activate this configuration" you effectively disable these options and make everything work inside WPASupplicant.)
So, if you simply want to get your WiFi connection up and running, this is overkill. Look at these articles first:
This article describes how to configure the builtin wpa_supplicant module to achieve almost any configuration goal you might have in terms of 802.1X, WPA, WPA2, etc. Please keep in mind that Stratodesk provides the configuration framework, but the effects of the changes is in the hands of wpa_supplicant.
Configuring network authentication is a hard task that requires knowledge of authentication mechanisms and protocols. We do our best to make it as easy as possible, but the complexity is inherent and there is not much we can do. You will probably need to interface with your colleagues who are doing the base-level networking to acquire connect information and certificates.
Contents
- 1 Configuration principles
- 2 Certificates
- 3 Testing
- 4 Rollout considerations
- 5 Configuration examples
Configuration principles
The basic idea is that every configuration file option of wpa_supplicant.conf translates to an option inside the Stratodesk configuration frame-work (and vice-versa). If there isn't an existing Stratodesk option, you can create use "user-defined options" to be able to express everything that wpa_supplicant can support.
It is important to understand that essentially you are essentially using the configuration mechanism to generate a configuration file for this third-party party program. That means you have to enter exactly the required syntax and keywords as documented in the wpa_supplicant manuals. See here for a detailed description of wpa_supplicant.conf: http://hostap.epitest.fi/gitweb/gitweb.cgi?p=hostap.git;a=blob_plain;f=wpa_supplicant/wpa_supplicant.conf
It is very important to know and keep in mind that the wpa_supplicant configuration is per-device! That is, you can have, for instance, one configuration for the wired ethernet interface, and another one for a builtin WiFi adapter.
On the client
You navigate the configuration path Network - Interfaces - (your interface) - WPASupplicant to access the configuration. You will find the basic parameters here that influence wpa_supplicant. Most important stuff is actually going into the "network config blocks", see below.
To tell the system to actually use the configuration here, please set the parameter "Activate this configuration" to on. Without that, your configuration will not be used.
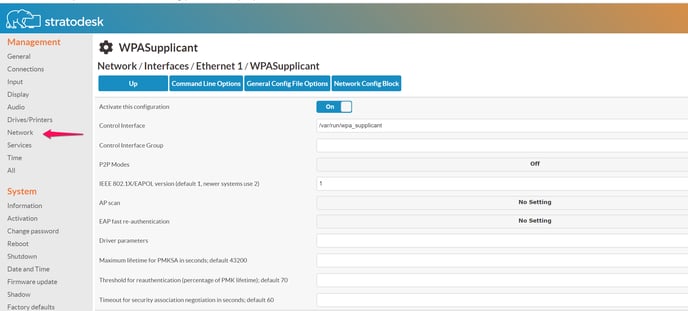
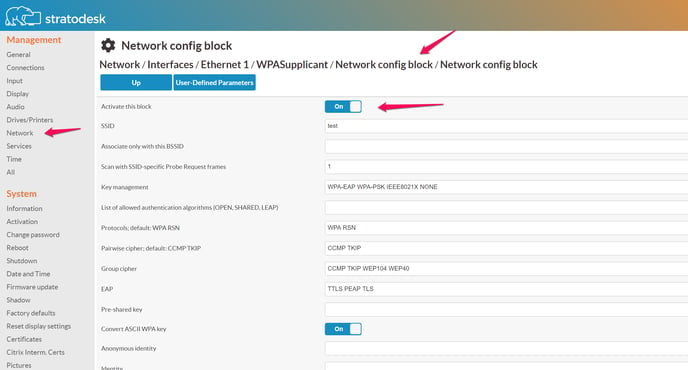
An interface's wpa_supplicant configuration can have multiple network blocks. wpa_supplicant will employ some black magic to determine which block to use (most of the time, it will use the WiFi SSID parameter), which can be influenced for instance with the "Priority" parameter. Most people will only have one or two network blocks. Wired interfaces typically are fine with one block anyway.
For wpa_supplicant to do actual work, you need to have at least one network block. So we suggest adding such a block, and configuring it right now.
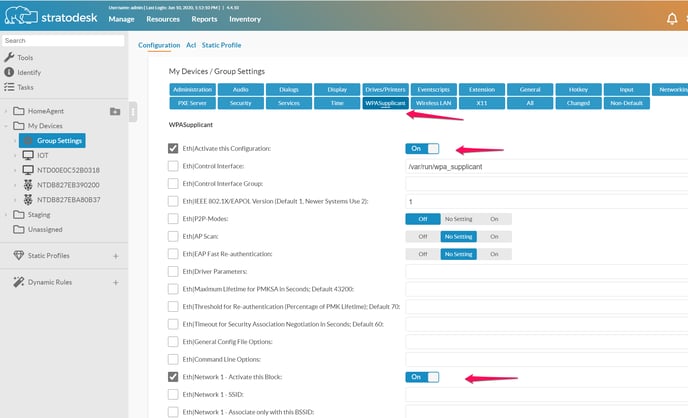
NoTouch Center
In NoTouch Center, you will find the WPASupplicant options in the "WPASupplicant" tab. You have the same configuration options, but the view is a bit different; NoTouch Center displays the Ethernet and WLAN interfaces in a list, with network blocks unfolded. So you do not have to explicitly create network configuration blocks, they already there when using NoTouch Center.
Keep in mind that a client that can not use the network because of authentication problems will also not communicate with NoTouch Center. That means, you can lock yourself out very easily. We suggest doing network authentication configuration locally first, and only if everything works then move on to the central management.
Even if you do the initial configuration locally, you will probably decide to manage your client infrastructure with NoTouch Center, for example to update your terminal server connection configuration, add user sessions, change the look&feel. So you must be sure that the configuration that NoTouch Center distributes does not destroy your network configuration (again - danger of locking yourself out). We suggest testing on a dedicated client machine first, move to NoTouch Center, make sure NoTouch Center configuration updates don't make anything worse, and then continue with your other devices.
Certificates
Some of the parameters in the WPASupplicant network block section refer to certificate files that must be present locally in the device. While the client displays an option box, in NoTouch Center you have to type in the file name. For the file to be available, you must upload it to the client.
You can easily upload certificates by connecting to the repurposed PC/thin client with a web browser on a different workstation. Most people just connect from their own PC/workstation/laptop by point their web browser to the IP address of the NoTouch client instance. It looks very similar to what you see when configuring the device locally. After login, you will find more options on the left side than locally, one is "Certificates" - that's the location to upload certificates. Any file uploaded here will then be visible inside the certificate choosing parameters. To make the upload work, many people first connect the system via an open LAN to upload basic things and then transfer the device to the secure network.
Another option is to have the client automatically fetch certificates on boot time (automatic certificate distribution) or copying it manually from a USB drive. Please read on here if you are interested: Certificates
Testing
You will have to reboot for the new configuration to take effect. We strongly recommend to work directly at the client and don't use remote login or central management because it is too easy to lock yourself out - but in most cases working locally is a must anyway, because how would you use remote login when the device doesn't have networking yet?
In the client's configuration menu select "Debug information" from the "Diagnostic" section, and then select "System Log", scroll down as far as needed. The output of the wpa_supplicant program will be there. Alternatively you can open a "Console" (also from the "Diagnostic" section), and type in the command logread.
Rollout considerations
You certainly do not want to preconfigure each individual device before use. There are some situations where you may have to touch each individual device first, such as when using static IP addresses or having individual client certificates per machine. While we generally recommend to avoid such complexity we understand that you have your reasons why you do so.
The easiest way would be to configure one device, fetch the configuration, put it on the USB or CDROM drive and then have this initial configuration applied to all devices that will be repurposed/installed. Please read on here for more information:
Another scenario would be to setup an unprotected LAN and configure your devices there, by having them connect to NoTouch Center, fetching the configuration, and then transfer them over to the final LAN (which could mean physical transfer or a change of VLANs).
Configuration examples
IEEE802.1X on wired interfaces
Create one network block, leave the SSID parameter empty. For this example, we assume you want to use both PAP and MD5, but no certificates.
Set the following parameters:
- Key Management: IEEE8021X
- EAP: TTLS MD5
- Identity: your user name
- Anonymous Identity: your username
- Password: your password
- Phase 1: auth=MD5
- Phase 2: auth=PAP password=mypassword
- EAPOL: 0
Of course you may have to change the example to fit your site-specific needs. Activate the block, and activate the configuration.
WPA with ASCII pre-shared key ("ASCII passphrase")
Create one network block, set the SSID, set the "Pre-Shared Key" to your passphrase, set the "Convert ASCII pre-shared key" to off. Make sure Key Management, EAP, Protocols, Pairwise and Group Cipher parameters are empty (not default).
Activate the block, and activate the configuration.
Plaintext connection
Create one network block, only set the SSID. Set "Key Management" to NONE. Make sure EAP, Protocols, Pairwise and Group Cipher parameters are empty (not default). Activate the block, and activate the configuration.
EAP-PEAP/MSCHAPv2 (typically used with RADIUS servers)
Create one network block and set the following parameters:
- SSID to your desired SSID
- Key Management: WPA-EAP
- EAP: PEAP
- Identity becomes your authentication user name
- Password is your authentication password
- CACert is your certificate (first upload/install it)
- Phase 1: "peaplabel=1"
- Phase 2: "auth=MSCHAPV2"
- Blank out Pairwise and Group Cipher and Protocols parameters.
Activate the block, and activate the configuration.
EAP-TTLS/EAP-MD5-Challenge
Create one network block and set the following parameters:
- SSID to your desired SSID
- Key Management: WPA-EAP
- EAP: TTLS
- Identity becomes your authentication user name
- Anonymous Identity becomes the user name for unencrypted use ("real" one is sent only within TLS tunnel)
- Password is your authentication password
- CACert is your certificate (first upload/install it)
- Blank out Pairwise and Group Cipher and Protocols parameters.
Activate the block, and activate the configuration.
EAP-TTLS/MSCHAPv2
This is equal to the EAP-TTLS/EAP-MD5-Challenge configuration, with the exception that one parameter has to be edited additionally:
- Phase 2: auth=MSCHAPV2"
LEAP
Create one network block and set the following parameters:
- SSID to your desired SSID
- Key Management: IEEE8021X
- EAP: LEAP
- Identity becomes your authentication user name
- Password is your authentication password
- Blank out Pairwise and Group Cipher and Protocols parameters.
Activate the block, and activate the configuration.
