NoTouch supports standard wireless protocols and authentication. Easily choose Wireless Networks while Mobile
NoTouch of course supports operating with Wireless LAN/WiFi/802.11/WLAN networks, with and without personal or enterprise authentication methods. Whenever a supported wireless network adapter is present, you can connect to available WiFi networks in your area. NoTouch offers three scenarios:
- A system administrators presets one or several allowed and configured wireless networks (see #Configuring wireless networks)
- Users can use a graphical tool to connect to any available network that they may have access to, such as in hotels, airplanes, cafes, ... (#Allow users to connect to WiFi networks)
- A third-party tool, Network Manager, that bypasses all of the regular NoTouch configuration methods
Contents
- 1 For the impatient: Just tell me how to get going
- 2 Configuring wireless networks
- 3 Allow users to connect to WiFi networks
- 4 Configuring Wireless LAN settings in NoTouch Center
For the impatient: Just tell me how to get going
For password authentication:
- Configure the network as a stored profile for and end user:
- In the local configuration application, click on Network, click on Interfaces, click on Wireless
- Enter your network's name (SSID)
- Set the Security to "WPA2 Personal"
- Set the password into the "Password/Preshared key"
- Click "Change", save, and reboot.
Configuring wireless networks
You can easily find out if your system has a supported wireless network adapter. Just open the local configuration application. Click on Network, click on Interfaces. If you see "Wireless 1" here - like in the screenshot below -, you are capable of using WLAN/WiFi.
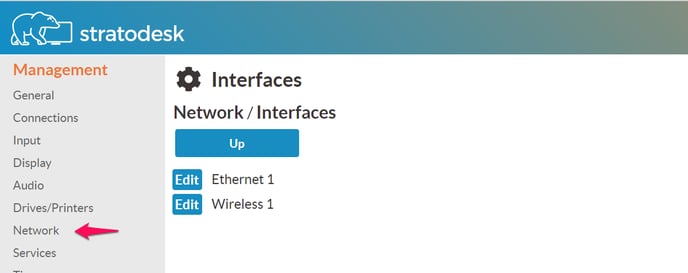
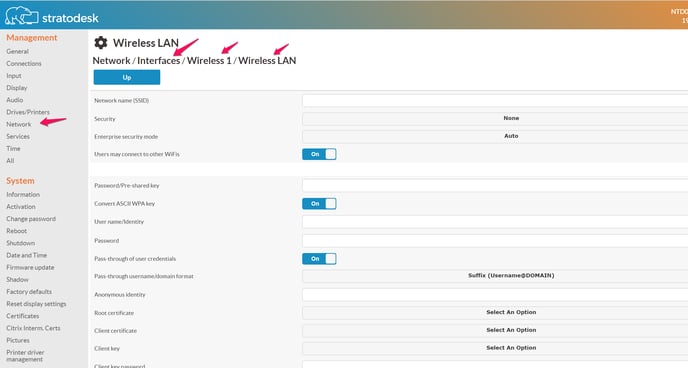
It is very easy to setup a wireless connection. Simply open the local configuration application or go to the "Wireless LAN" tab in NoTouch Center. If on the client, click on Network, click on Interfaces. Click "edit" near the "Wireless 1" interface.
There are two parameters that must be set in any case:
- Network name (SSID). Set this to the SSID of your wireless network.
- Security. Set this to your desired authentication/security method. If you just have a "WiFi password", then select "WPA2 Personal". If you have certificates or username/password then you'll rather use "WPA2 Enterprise". Possible values are:
- None. No security is to be used. This is rarely used.
- WEP. The old WEP standard. Almost never used, if your network administrator still uses that, tell them to switch to WPA2.
- WPA Enterprise. This will connect with either WPA, or its stronger WPA2 successor, and connect with an enterprise security mode that is further specified in the "Enterprise security mode".
- WPA Personal. This will connect with either WPA, or its stronger WPA2 successor, and connect with a simple "WiFi password" that you supply in the "Password/Pre-shared" key parameter.
- WPA2 Enterprise. This is will use today's strongest available security, WPA2, only and connect with an enterprise security mode that is further specified in the "Enterprise security mode".
- WPA2 Personal. This is will use today's strongest available security, WPA2, only and connect with a simple "WiFi password" that you supply in the "Password/Pre-shared" key parameter. In this case, you do not have to set "Enterprise security mode" parameter. This is what you use when you are told a simple "WiFi password".
Password/"Personal" authentication
Type in your WiFi passphrase or password into the parameter "Encryption Key/Password". This is also known as the "Pre-Shared Key" or simply PSK. Make sure you don't mistype it. Repeatedly mistyping a passphrase is the #1 error cause for failing WiFi connections!
In most cases you are fine and can click on "Change" and later on save the configuration and reboot.
Enterprise authentication
The Enterprise security mode parameter defines what kind of enterprise security you have in your network. If you are unsure, please consult with your network administrator. The following options are available:
- PEAP-MSCHAPv2 (RADIUS). This is the most common authentication method; most probably this is used if you have a username and a password to connect to a network.
- EAP-TLS. This is probably the second most common method and typically this is used when you have a client certificate.
- TTLS. Tunneled Transport Layer Security, or EAP-TTLS will authenticate using a certificate.
- TTLS-MSCHAPv2. This runs TTLS to authenticate the network with a certificate, and inside the tunnel MSCHAPv2 to authenticate the user with a username/password combination.
- LEAP. Lightweight Extensible Authentication Protocol, a protocol developed by Cisco.
Note: These methods are very complex and we assume you simply want to connect without earning a degree first. So we assume you have either certificates or credentials ready and your network admin has informed you about the methods to be used. If you are interested in the inner workings of WiFi security, we suggest to start reading about EAP-Extensible Authentication Protocol, RADIUS and potentially wpa_supplicant.
Username/Password
For username/password authentication scenarios, there are three ways how you can handle that:
- Pre-configure/store user credentials in the configuration. This would work either with
- Machine accounts, e.g. for a public machine that has a machine username and password
- User's desktops where the user would never change (quasi-private machines).
- Pass-through the user's VDI credentials to the WiFi stack.
- Both. In that case, when nobody is working at the machine, the pre-configured username/password will be used to get on the network, if somebody logs in the connection would be reset and a new connect based on the user's credentials will be made.
Preconfigured/stored credentials
These parameters allow to store credentials on the machine:
- User name/Identity. The username to connect with.
- Password. The user's password (not to be confused with the WLAN passphrase).
- Anonymous identy. Some connection modes require or allow to set an "anonymous identity". Use this parameter if you have such a requirement.
Note: NoTouch does encrypt stored passwords, of course. However, all these mechanisms can be broken, it's just a matter of investing enough time and money. We suggest to not rely on stored credentials.
Username/Password pass-through
For several connection modes, NoTouch shows a login dialog and lets the user type in their credentials: username, password and potentially a login domain. These credentials can be passed on to the WiFi stack, resetting the existing WiFi connection and authentication with these credentials. For this to happen, it must be enabled both in the network configuration and in the connection parameters.
These parameters govern the pass-through:
- Pass-through of user credentials. Set this to on (default), if you want the functionality being enabled. Note - this alone is not enough, you have to enable it in your connection as well.
- Pass-through username/domain format. Define if the domain should be passed on the WiFi stack in prefix (domain\username) or suffix (username@domain) notation or not at all.
- These parameters in your connection's Extended section:
- Pass-through of user credentials. Set this to on, if you want the pass-through to happen. By default, this is off.
- Reset wireless connection. Set this to on, if you want your credentials to be passed on the Wireless connections. By default this is off.
So to summarize, for pass-through to happen, you need to go to the Connection / Extended parameters and enable at least "Pass-through of user credentials" and "Reset wireless connection". Read more about this here:
When the VDI connection exits, the WiFi connection will be reset. In that case, the preconfigured/stored credentials will be used, if some are defined, until the next users logs in.
Certificate-based authentication
Please refer to Certificates to find out how to upload and distribute certificates and key files.
- Root certificate. The root certificate of your authentication authority.
- Client certificate. The certificate of the client to be presented to the server.
- Client key. The certificate's key file. Without such a key the server would not know if this client is the rightful owner of the certificate, so this can not be omitted.
- Client key password. The certificate's key file password/decryption key in case the key file is encrypted.
Other parameters
The following parameters are very special and should be left on their default values in normal operation. Only if you have a special scenario, your network installation requires specific settings or you are experiencing problems you should change these parameters:
- Convert ASCII WPA key. This switch defines if the passphrase should be converted to hex key format or not. In most cases your setup will work either way, but if you can't connect, please switch this parameter to the other value.
- Scan with SSID-specific Probe Request frames. The default value here is "1" which means that the system will send such SSID-specific probe requests. This makes network scanning a bit slower, but allows to detect "hidden" SSIDs. If you have a hidden SSID, most probably you need to this have on 1. You may set this to 0 which improves scanning speed. You can try - if it doesn't work, revert back to 1.
- PEAP label version. Defines if version 0 or version 1 of PEAP labels should be used. The default value of "auto" will chose the best one.
- EAP fast re-authentication. By default, fast re-authentication will be used, so this switch can be used to disable this.
- IEEE 802.1X/EAPOL version (default 1, newer systems use 2). Governs the EAPOL version to be used.
- Pro-active key caching. Governs if keys should be cached pro-actively. If on "No setting" (default), the system will use the best approach.
- Maximum lifetime for PMKSA in seconds. The default value, if left empty is 43200.
- Threshold for reauthentication (percentage of PMK lifetime). The default value, if left empty, is 70.
- Timeout for security association negotiation in seconds. The default value, if left empty, is 60.
- Access Point scanning/selection. This parameter defines the software method how to scan for access points. There is almost no scenario where a change could make sense, so leave it on the default.
- Old auth mode (Deprecated). This refers to the way WiFi was configured in older releases up to 2.36, at that time the "Auth mode". This is deprecated and for compatibility only (to catch setups where clients are newer than a global configuration). Do not set this on a newer system.
- Channel. Here you can select a specific WLAN channel. There is no reason to set this on the client in 99.99% of all cases (if you want to change channels, you would do this in the access point).
If you need to create a more complicated setup, such as using an authentication method that is not present here or creating more than one preconfigured WiFi setups, please read on here: WPASupplicant
Allow users to connect to WiFi networks
From NoTouch OS version 3.3.635 onwards, Network Manager is enabled by default, which provides an easier way for end users to connect to wireless networks. For earlier versions of NoTouch OS, you can enable this by following the instructions in this knowledge base article.
To connect to a wireless network, click the network manager icon in the task bar, and search for the preferred network. This might also appear under available networks.
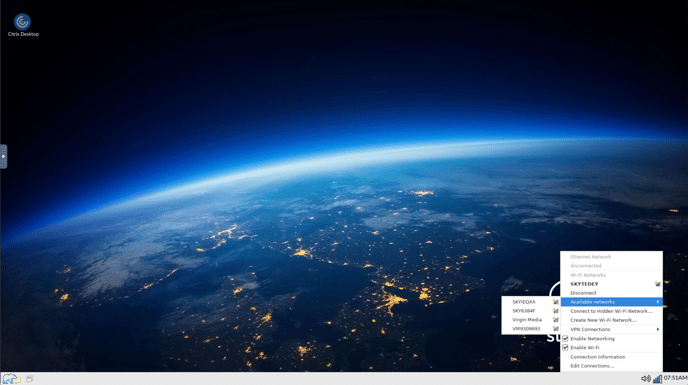
When prompted add the SSID password to join the network.
Note: Many WiFi "hotspot" providers require some sort of check-in or acceptance of terms and conditions using web. It is advisable to offer a Firefox connection for users to accomplish that.
More options:
- Hidden networks. If you want to connect to a hidden network (i.e. one that does not show up in the list because the system administrator has disabled this for security reasons), use the "click here to join other network" link that allows you to type in both network name (SSID) and password.
- Manage configured networks. This dialog allows to remove remembered networks. If you are on the road for a long time, many stored hotel and cafe WiFi profiles will be stored. Use this to clear this list and delete unnecessary entries.
- Reset wireless interface. If you believe something has gone wrong or the wireless appears stuck (very rare), then you can simply reset the WiFi stack and adapter without having to reboot the machine.
Configuring Wireless LAN settings in NoTouch Center
There is nothing special about doing the configuration in NoTouch Center. The parameters match exactly. Please use the "Wireless LAN" subsection in NoTouch Center to configure the WiFi/Wireless LAN configuration.
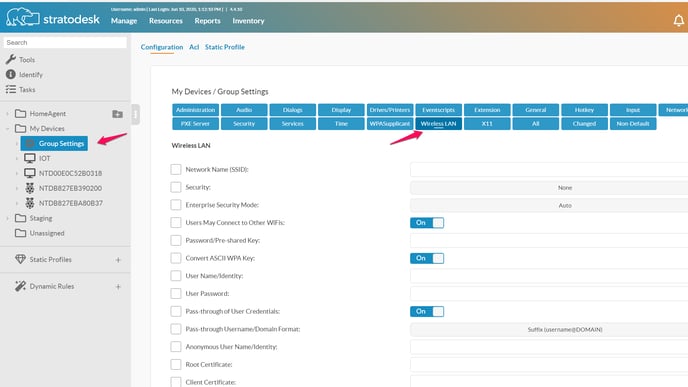
However, if you have a complex authentication setup then you may encounter a chicken-egg problem that your client machine would need WiFi configuration to connect to the network in the first place to be able to contact NoTouch Center. However, with NoTouch there is an easy solution:
- Configure the Wireless LAN settings perfectly in NTC
- Also configure the Wireless LAN settings locally on a template client (not joined to NTC yet)
- Use the Configuration preload mechanism
This approach combines the best of both worlds - it will allow newly repurposed machines to be online in your network without manually configuring each of them, and later changes can be done centrally and comfortably via NoTouch Center.
