Here are some leading practices on configuration and hardening of the most current Firefox Browser which is available in NoTouch
Stratodesk makes sure NoTouch has latest versions of the Mozilla Firefox web browser integrated, with a PDF viewer and Adobe Flash plugin. People use the Firefox for example to:
- access web-based enterprise applications, exclusively or next to VDI connections
- build a web kiosk system with custom hardware and Stratodesk NoTouch
- connect to Citrix or other VDI connections that use the browser as frontend.
Using a browser can compromise your IT security. We want to make you aware of the dangers before you use Firefox - please read the section on #Security considerations.
Depending on your security requirements, organization size and culture and trust in your end users we may even advise you to not use Firefox at all!
As a side note, if you don't like Firefox, you can alternatively use Chromium.
Contents
- 1 Basic configuration
- 2 Write protection
- 3 In-depth configuration
- 4 Getting information about Firefox
- 5 Certificates
- 6 Creating a custom Firefox profile
- 7 Citrix Web frontend
- 8 Flash Player
- 9 Java
- 10 PDF
- 11 Security considerations
- 12 Updating Firefox without updating the OS image
- 13 URL-based lockdown scenarios
Basic configuration
This assumes you are familiar with configuring NoTouch locally or via NoTouch Center and especially how server connections are created and configured. Making your endpoint start a Firefox web browser is easy and requires only two steps:
- Create a connection and set the connection mode to "Firefox"
- If, and only if you want to start the browser start with a specific URL, such as your company web page, type that URL into the "Connection target" parameter.
This is enough to get a Browser setup - it's really that easy. From there you can of course change many different options. For instance, you can configure the client to come up automatically after boot time; and you can modify all Firefox options (submenu Firefox web browser) under the Connection options. See below for the configuration possibilities.
Important note: In the default configuration, Firefox is not allowed to do a lot, it can not even access the sound/audio device. Please set the "Force execution as root" parameter to on in the Connection settings and read below about the implications.
Write protection
By default, all writes done by the web browser, such as changing preferences inside Firefox, saving bookmarks, cookies, web cache etc. are all written to the local RAM disk. When closing Firefox and restarting later, all these modifications will be gone. A reboot will clear out even downloaded files. This makes NoTouch a great web kiosk system by default. This behavior can be modified as well as other aspects of the system.
In-depth configuration
Refer to the submenu "Firefox web browser", or simply "Browser" in NoTouch Center. Advanced aspects regarding the browser can be found there. 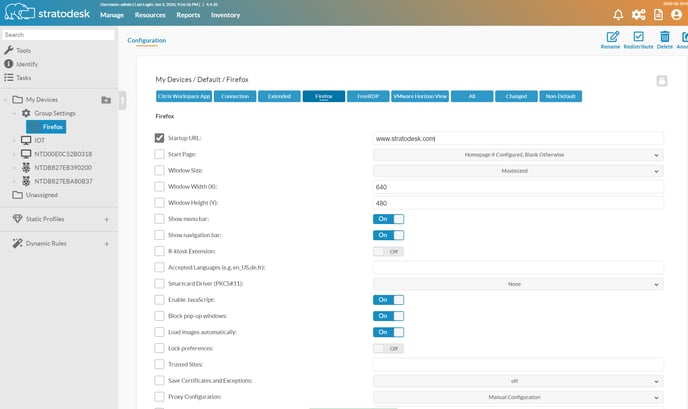
Start page behavior
The "Startup URL" parameter contains the URL that the browser should launch at startup. It will preempt any setting in the Connection target parameter; that means, if both the Connection/Connection target parameter and the Firefox-Browser/Startup URL parameters are set, the Startup URL parameter will win.
The "Start page" parameter can override the behavior and display a blank page, even if a startup URL is set. By default, a blank page will shown only when both the Startup URL and the Connection target are empty.
Screen layout and toolbars
By default, Firefox will be run maximized - Maximized means that there is still the task bar visible as well as the window title bar. Other options would be "fullscreen" - without window title bar, without window borders, and covering all screen including the task bar with its start menu; or "X/Y size", meaning run in a window of size X pixels horizontally and Y pixels vertically. If you select "X/Y size", you should enter your desired Window height and width into the appropriate parameters. With the Window size "Maximized" or "Fullscreen", both options "Window width (X)" and "Window height (Y)" have no effect (of course).
Three separate options allow to control appearance of tab bar, navigation bar and menu bar.
Content options
There are parameters to specify the accepted languages - a comma-separated list in standard locale format, such as en or en_US for English or English/USA. The order matters! So for example if you would prefer to see Web pages in Italian, but speak English as well, you could enter it,en. French Canadians might want to enter fr_CA,en_CA,en_US to have French set as desired language with fallback English (Canada) and then English (US).
Furthermore you can block automatic loading of images, pop-up windows and Javascript.
Parameter lock
Accessing the preferences from inside Firefox, via the Preferences menu entry, would allow a user to change preferences, at least for the current session (remember, writes are not persistent by default). The parameter "Lock preferences" will lock preferences that are set, i.e. the Firefox preferences dialog will not allow them to be modified.
Proxy settings
The proxy settings here match the settings you would have when configuring Firefox via its native preferences dialog. If you set the proxy type to "System", this connection will inherit from the system-level proxy settings. Firefox proxy settings must be specified as host:port to have an effect, otherwise they will be ignored.
Note that the Citrix Receiver has its own proxy configuration but can inherit the Firefox configuration settings. See Citrix Receiver configuration#Proxy settings for more information.
Command line options and UserPrefs
There are two submenus within the Firefox browser options that allow for even more advanced configuration, going beyond what is available in the NoTouch menu:
- Command line options, referring to the options the Firefox application (Linux binary) will be launched with
- UserPrefs, options that will go verbatim into the prefs.js file.
If using NoTouch Center, these options are text fields that are able to contain comma-separated lists.
Getting information about Firefox
As with normal Firefox, there are several special URLs that you can use to get information out of
- about: shows information about the Firefox version
- about:plugins shows plugin version information
- about:config shows and allows to edit configuration options. It will display a Mozilla-authored warning about voiding warranty before doing so.
Please note that our PDF viewer, xpdf, is not a plugin but a helper application - thus it won't be shown in the about:plugins dialog.
Certificates
Firefox includes the most well-known root certificates - Firefox has its own certificate store, independent of the NoTouch certificate store. Only if there was a very new certificate vendor on the market or you are using a private or self-signed certificate, you might have to upload a certificate to the NoTouch system. As of NoTouch 2.35.60, two methods exist for adding custom certificates:
- Add certificates to NoTouch. From NoTouch 2.35.60 on, the Firefox web browser will add custom certificates to its own store. Uploading them to the system via the standard NoTouch interface is preferable over the other method, since these certificates can also be used by the Citrix Receiver, the VMware Horizon View client and other third-party applications.
- Go the web page, when Firefox display the warning, save the security exception. Since such an exception would not be saved by default, do it within the creation procedure of a custom profile (see below).
Creating a custom Firefox profile
By default NoTouch does not store Firefox settings, cache, cookies, etc persistently. It is very easy though to modify that behavior, in fact there is even a procedure to let an administrator create a custom profile and then make it available to users, but disallowing users to store changes. This is only necessary if you want to make changes to your
Firefox configuration that can not be done by the NoTouch configuration system.
Note: Do not confuse this feature with the ability to modify templates. Templates are used to generate an application's configuration - the profile feature however takes already-generated configuration files, allows to modify them and stores them.
Make NoTouch save all user changes to Firefox
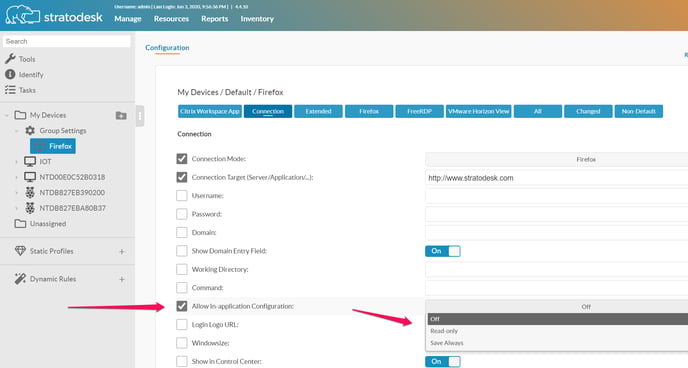
Disabling the NoTouch write protection is easy: Under the Connection options tab, there is the parameter "Allow in-application configuration". This parameter is set to "off" by default. If you set it to "Save always", NoTouch will store all changes made, such as bookmarks, history, cookies, cache persistently.
This setting is good for one or just a few trusted users. We do not recommend this for a public terminal. A more sophisticated approach is given right below:
Create a custom Firefox profile
Creating a custom Firefox profile is easy:
- You, being the system administrator, enter the local configuration of the NoTouch OS. Under the Connection options tab, there is the parameter "Allow in-application configuration". This parameter is set to "off" by default. If you set it to "Save always", NoTouch will store all changes made, such as bookmarks, history, cookies, cache persistently.
- Now you can make all modifications you want, you can even install Firefox extensions (Administrator Mode).
- When done, quit Firefox and go back into the NoTouch configuration and change the "Allow in-application configuration" to "read only". From now on, your configuration will be applied at every Firefox start, but any changes made are not saved (User Mode).
Distribute Firefox profile via NoTouch Center
You can use NTC's built-in Profiles feature to also distribute a Firefox profile. Please note that Firefox stores all its configuration inside of the "savecfg" folder of your config file, so if you just need to supply Firefox settings, it's enough if your profile contains just this one folder. Also, don't forget that you've got to create a browser connection named exactly like the one that was used to retrieve the config file from so that NoTouch Center is able to match the configuration to said connection!
For this to work correctly "Allow in-application configuration" must be set to "Read-only" in NoTouch Center for the Group settings of the device receiving this Profile
Citrix Web frontend
Firefox in NoTouch contains the Citrix ICA plug-in, that runs the Citrix client when receiving .ICA files, such as when connection to XenApp or XenDesktop. That means, a browser connection in NoTouch is also potentially a Citrix connection, as many people use the browser to connect to Citrix. To allow Citrix configuration to be made also for browser connections, there is the "ICA" subtree under the Connection options of a browser connection. It resembles the options as if you would configure a Citrix connection.
Please note that values sent by the server in the connection ICA file will always override NoTouch settings. If you feel that something doesn't work, look on the server first!
Side note: Do not try to make the system use the Java ICA client - NoTouch has a native Citrix Receiver included that performs much better.
Flash Player
The Adobe Flash plugin is integrated and will work out-of-the-box.
Updating the Flash Player plugin
NoTouch versions will always work with the latest available Flash plugin at the time of their release. That means that downloading a new, updated NoTouch OS image will also give you a new, updated Flash player plugin. However, Flash updates come irregularly and frequently, you may want to update the Flash player plugin on your own without actually updating the whole NoTouch OS image. From NoTouch OS 2.40.400 onwards you can update Flash on your own:
- Download the "Linux 32-bit tar.gz" Flash package from the official Adobe download page (at the time of writing this is https://get.adobe.com/flashplayer/otherversions/
- Place it - without any modification - on a web server in your organisation. If you don't have one, see Hosting files (VA) and Hosting files (NoTouch Center)
- Navigate to the "Extension" parameters and look for the "Flash Player URL" parameter. Enter the URL that leads to this file.
- Reboot the client.
Troubleshooting: On the client, or via its web interface, open the Configuration, click on "Debug information" and then on "Cache". You will see error messages and status information there.
Notes:
- This mechanism needs both local disk space and RAM in excess of the package size; thus this will only work if you have enough RAM and disk/flash space available. It will probably not work on space-constrained older Thin Clients with less than 1GB of Flash or RAM.
- This method works with Mozilla Firefox packages as they were as of January 2016. If Adobe at one point decides to change their package format, this method may not work any longer.
- There is another, similar sounding parameter named "Citrix Flash player URL" in the Extension parameters. That one however updates the Flash player for the builtin Citrix Receiver only, not for the browser.
Java
NoTouch supports Java; to be more precise: NoTouch typically includes a version of the Java Runtime Environment, capable of executing Java applications, Java WebStart and, relevant to this page about Mozilla Firefox, Java applets. Not all NoTouch images have Java included as it is big and not so widely used. If your system has Java, you will see it in the about:plugins list and Java applets will work out-of-the-box.
When clicking on a PDF file, NoTouch will launch xpdf, a free and fast PDF viewer.
Security considerations
With VDI connections, such as RDP, Citrix, VMware etc. almost no interaction happens between applications inside the user desktop and NoTouch. Running a local browser is different, it is indeed a local application executing code locally! Firefox allows your users to download Linux applications, configuration files, thus modifying the system, install malware, spyware, keyloggers. Yes, typical Windows malware like Win32 code will not work, so most standard attacks fail but you can not rely on that.
In a nutshell, we strongly suggest to put filtering proxy servers in place or otherwise confine Firefox to, say, a Citrix web portal, or similar. (see #URL-based_lockdown_scenarios)
NoTouch has several mechanisms in place to prevent permanent changes made by the user or a malicious software loaded by the user. These mechanisms are not unbreakable, but they provide reasonable protection against common attacks. There are two potential attack scenarios:
- A local, malicious user with physical access to the machine may outsmart the Linux security mechanisms since Firefox offers more interaction with the system than a regular VDI client
- A local user could open a prepared website that exploits a Firefox security vulnerability which in turn allows to
Both attacks could lead to keyloggers being installed (remember, there are no user documents to be stolen on the Thin Client, so the most valuable asset are probably user's keystrokes).
To mitigate the risks as much as possible, we suggest:
- Make sure the "Force execution as root" parameter under Connection->Extended is "off".
- Public stations, such as reception-floor info terminals, should be placed in a separate subnet with filtered Internet or server connectivity but no access to the corporate network and reinstalled regularly or even PXE-booted.
- Corporate stations, such as for end users allowed to use the Internet, should be placed behind a filtering proxy server (as should any Windows PCs anyway). If PCs can be accessed by other users (e.g. unlocked cubicles) a certain rest risk can not be eliminated (like on Windows PCs actually).
Updating Firefox without updating the OS image
Note: Available on x86 (PC) only - not for the Raspberry Pi.
NoTouch versions will always work with the latest available Firefox browser at the time of their release. That means that downloading a new, updated NoTouch OS image will also give you a new, updated Firefox browser. However, Firefox updates come frequently, you may want to update the Firefox browser on your own without actually updating the whole NoTouch OS image. From NoTouch OS 2.40.400 onwards you can update Firefox on your own:
- Download the "Linux 32-bit tar.bz2" Firefox package from the official Mozilla ESR download page https://www.mozilla.org/en-US/firefox/organizations/all/
- Note: Currently, as of late 2016/early 2017 NoTouch requires the Firefox 45 ESR (Extended Support Release) packages. These feature all the security upgrades, but are more compatible.
- Note you can get earlier versions than 45 should you need to downgrade from the normal Mozilla web page (at the time of writing this is https://www.mozilla.org/en-US/firefox/all/
- Place it - without any modification - on a web server in your organisation. If you don't have one, see Hosting files (VA) and Hosting files (NoTouch Center)
- Navigate to the "Extension" parameters and look for the "Firefox URL" parameter. Enter the URL that leads to this file.
- Reboot the client.
Troubleshooting: On the client, or via its web interface, open the Configuration, click on "Debug information" and then on "Cache". You will see error messages and status information there.
Notes:
- This mechanism needs both local disk space and RAM in excess of the package size; thus this will only work if you have enough RAM and disk/flash space available. It will probably not work on space-constrained older Thin Clients with less than 1GB of Flash or RAM.
- This method works with Mozilla Firefox packages as they were as of January 2016. If Mozilla at one point decides to change their package format, this method may not work any longer.
URL-based lockdown scenarios
No Internet, just Intranet or connection broker only
If you want your users to be able to internal websites but not the free Internet at all, there is a simple trick that works without add-ons or proxy servers. This is useful for people who want to use the browser just for the Citrix web interface, and maybe a few other known-good internal URLs.
- Enter the Firefox configuration, and specify non-existing HTTP and HTTPS proxy servers, for example 1.1.1.1
- Add your known good URLs to the "No proxy for" parameter. This may include your whole intranet domain, for example .intranet.mycompany.com, or just the hostname of our connection broker (Citrix/VMware/etc. host)
- Set the "Lock preferences" parameter to "on", to avoid users disabling the fake proxy server.
This method is so simple as effective. Your allowed URLs will work, and everything else will end at an error message.
Allow Internet, but no obscene or illegal material
In this case we would advise you to use a filtering proxy server. As the definition of obscene varies by culture, and the definition of illegal varies by legislation, it will be impossible to solve it on a Thin Client.
